Have you been facebooked? Where not to look for an answer!
Update 1: As expected, the website in question has been taken down as of 7PM CT, Tuesday April 6 2021
Update 2: Some readers pointed out that HIBP is doing the same thing. That is correct. Actually, in the case of HIBP, they are sending the actual phone number, without obfucation, in a GET request! But I guess thats the point? HIBP, unlike this website, is not making a incorrect claim that it will not have access to your phone number!
Original Post
Internet is an interesting place! A ship blocks the suez canal and someone quickly builds a website to answer one simple question in everyone’s mind: is the ship still stuck? (https://istheshipstillstuck.com/). Yayy! A win for the internet!
A week later, troves of Facebook data gets leaked and someone builds a website to answer one simple question in everyone’s mind: have I been Facebooked? (https://haveibeenfacebooked.com/) Yayy!? Err… maybe, kinda, actually it depends on how you treat your phone number.
Before we continue, you may ask: how can I find out if my data has been leaked in the Facebook breach? The answer is: use HIBP, or https://haveibeenpwned.com/. They’ve got the technical (and social) bits of this process right!
What gets sent back to server
The claim made at the website is that your phone number never leaves the browser. That is absolutely correct. Also, that means nothing.
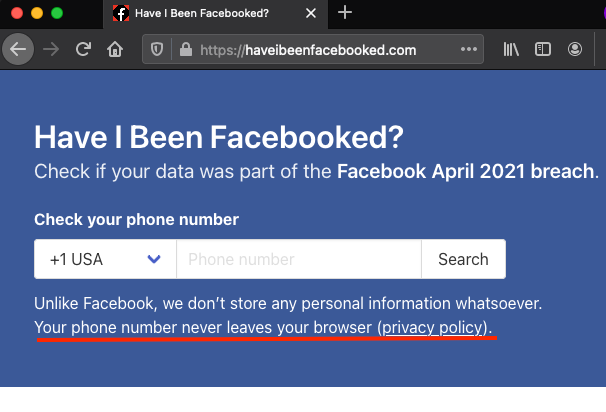
In this example below, I provide +1(111)111-1111 as my phone number. On a cursory look, what leaves the browser when I press the “Search” button looks like some sort of a cryptographic hash.
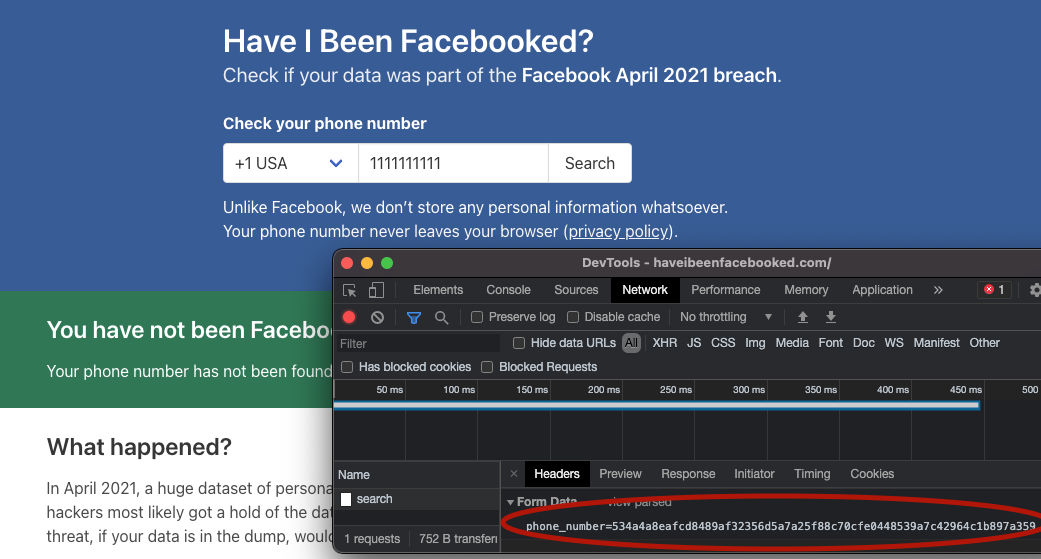
Does it pass a quick smell test? Spoiler Alert: No
The authors of this website have access to this string. Just asking google what that string means suffices here. No rainbow tables, no GPU crackers, no reverse engineering. As google helpfully states, the string that gets sent to the backend is a SHA256 hash of the phone number. In this case, google correctly shows the preimage of that hash is 11111111111
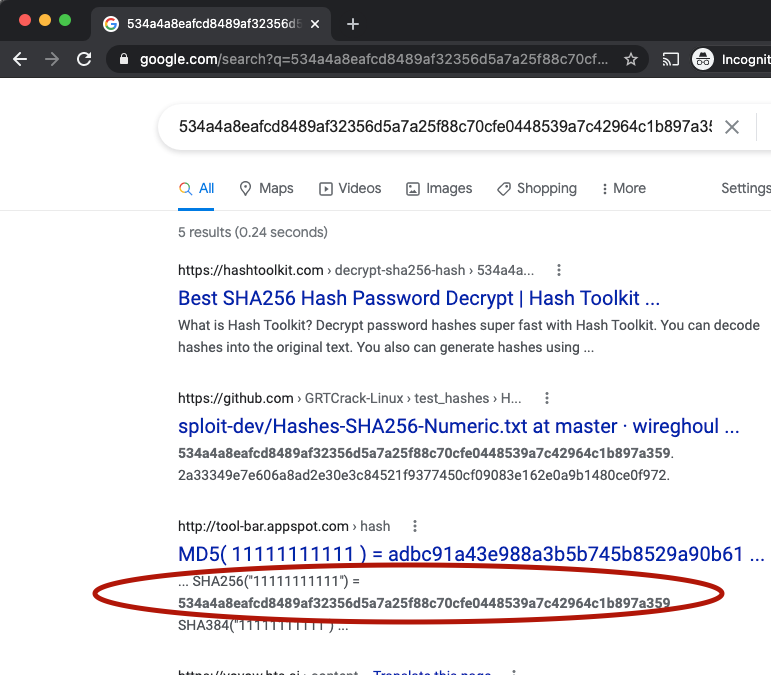
The verdict
It only takes a little effort to pre-compute all the phone numbers and their corresponding hashes to create a hash->phone number dictionary. Given there are only half a billion records in the leak, such a computation might just take a couple of seconds on an average laptop.
If you don’t care about your phone number being available to the developers - which by the way is perfectly fine - then go ahead and plug in your number.
Epilogue
The claim by the website that the phone numbers entered are not being sent to the backend gives a false sense of privacy. The fact is that what gets sent to the backend can be trivially reversed to the original phone number.
By the way I am still surprised Facebook has not sent them a Cease-And-Desist for domain name infringement yet!